The ultimate network security package.
An essential network firewall, plus protection for web and email gateways, laptops and mobile devices.
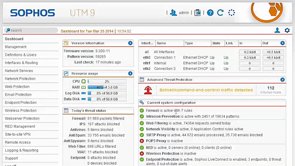
Sophos UTM gives you complete security from the network firewall to endpoint antivirus in a single modular appliance. It simplifies your IT security without the complexity of multiple-point solutions. The intuitive interface will help you quickly create policies to control security risks. And clear, detailed reports will give you the insight you need to improve your network performance and protection.
What’s New in UTM Accelerated (9.2)
The new Sophos UTM Accelerated (9.2) offers enterprise-grade protection in a single box. No compromise. Better performance.
- Advanced Threat Protection
- Smarter Secure Web Gateway in a unified product
- Simpler email encryption and DLP
- Faster IPS, optimized for the best performance
- Safer Web Servers with reverse-proxy authentication
Of course, there are many more features for you to explore – such as our two-factor authentication, or web filtering for Sophos Enterprise Console managed endpoints.
Flexible Deployment
Sophos UTM gives you complete security—from the network firewall to endpoint antivirus—in a single modular appliance.
- Install as hardware, software or a virtual appliance or even in the cloud
- License our protection modules individually. Or, you can choose one of our pre-packaged licenses
- Centrally manage multiple appliances through IPsec VPN tunnels with our Free UTM Manager

Usable Threat Management
At Sophos, simplicity is our mantra. You’ll have complete control over all the security features you need all in one place, with none of the complexity.
- Every feature is available on every appliance
- Manage multiple UTMs with our free Sophos UTM Manager
- Includes on-box reporting for real-time and historical data
And because it’s so simple, you’re never more than a couple clicks from completing your tasks.
Complete On-Box Reporting
Our built-in reporting means you’ll know exactly what’s happening with your users. Fix problems fast and shape your policies, keeping your users secure while boosting network performance. And, you get detailed reports as standard, stored locally with no separate tools required.
- At-a-glance flow graphs show usage trends with predefined and customizable reports, providing key web activity
- Report anonymization hides user names, requiring the four-eyes principle to unhide them
Lightning Performance
Our hardware appliances are purpose built, high-performance devices. They integrate our security applications with a hardened operating system (OS) on optimized Intel-compatible server systems.
- Flexible and scalable hardware and software tailored to your needs
- Optimized for best performance in real-life usage scenarios
- Best performance, no matter which deployment method you choose
Centralized UTM Management
Whether you have a few UTMs or a few hundred, we make it easy to centrally manage and monitor your entire estate with a single pane of glass.
- Easily manage multiple UTM installations from a single console
- Configure web, email and network filtering policies across multiple sites or customers
- View threat, network and hardware resource status across all your UTMs at a glance
- Aggregate reporting across all your UTMs or view just a single installation
Two-Factor Authentication
Add an additional level of security to access many key areas of the UTM. Our one-time password solution requires no infrastructure and gives you secure access to the WebAdmin, User Portal, SSL VPN, IPSec VPN, Wi-Fi Hotspots and SSH login.
- Compatible with all OATH authentication systems plus YubiKey
- Supports soft tokens, hardware keys and mobile applications
- Mobile users just scan the QR-code to get their one-time password
Self-Service User Portal
Our self-service user portal helps users help themselves, reducing the workload on your help desk. It provides personalized email and remote access services to authorized users—and it’s simple to use.
- Access and manage email quarantine to release messages inadvertently marked as spam
- Create email sender whitelists to stop legitimate mail being quarantined, and create POP3 accounts too
- Download remote access client software and configuration files.(SSL, PPTP, L2TP, IPsec Road Warrior)
- Change user preferences such as the portal password
Advanced Threat Protection
Our Advanced Threat Protection (ATP) combines multiple technologies to add an additional layer of defense against targeted attacks on your network.
- Uses layered protection to effectively prevent APTs, command and control traffic and targeted attacks
- Performance-optimized Intrusion Prevention System (IPS) identifies and blocks attacks through deep-packet inspection
- When combined with Web, selective analysis of unidentified traffic in a cloud sandbox helps to constantly improve the threat data provided by SophosLabs
Customizable Web Filtering
Select from over 35 million sites in 96 categories to create safe web browsing policies—so you can minimize legal concerns around inappropriate content and maximize productivity.
You can set policy by users and time, using a variety of authentication options including IP or Mac Address, Active Directory SSO, eDirectory SSO and LDAP. And, it syncs with UTM Endpoint Protection and the Sophos Enterprise Console, providing a single web security policy for users everywhere.
Web Malware Protection
You get the most advanced web threat protection:
- Our high-performance web malware engine inspects all web traffic in real-time
- Advanced techniques like JavaScript emulation block the latest web threats before they reach the browser
- SophosLabs continuously updates our threat intelligence via the cloud, keeping you ahead of new and emerging threats
Complete Email Protection
Block spam and viruses while keeping your sensitive data safe.
- Let users manage their spam quarantine and search a personalized mail log
- Antivirus scanning keeps infected emails out of your mailbox
- Protect your confidential emails and sensitive data from unauthorized access with our unique email encryption and DLP
Powerful Webserver Protection
You can quickly harden your web servers and apps against common attacks and ensure regulatory compliance with our web application firewall. Get instant protection without changing your web server code and no training required for admins or web developers.
You get a full-featured reverse proxy with SSL offloading and a variety of authentication options to add an extra layer of security to Exchange – it’s the perfect replacement for TMG.
Built-in Wi-Fi
You can set up, manage and secure wireless networks in just minutes with the UTM’s built-in wireless controller. Use the voucher-based system or backend authentication to control access and usage.
- Set up wireless hotspots and guest access with a simple, customizable voucher-based system
- Access Points need no manual configuration and are instantly protected by the UTM
- Repeating and bridging functionality extends Wi-Fi to harder to cable areas
Easy Site-to-Site VPN
Sophos RED (Remote Ethernet Device) provides secure remote access to your off-site locations. It’s the first security gateway that requires no technical skills at the remote site. Once installed, it forwards traffic to the UTM for complete security.
Our Secure SSL or IPsec VPN clients provide mobile and home workers with secure remote access from any location at any time. And our unique UserPortal means users can install VPN Clients and manage their spam too.
Proven Endpoint Antivirus
Extend protection to your desktops and laptops with antivirus, device and web control in one.
- Scans files, webpages and devices blocking or cleaning threats
- Device control reduces the risk of data loss and malware by managing removable devices
- Built-in URL filtering makes sure users get the same level of web protection outside of the office as they do inside
Dynamic App Control
In a couple clicks you can protect your employees from web threats and control their time online.
- A graphical flowmonitor and dynamic reports let you check on the fly to see if your policy is working and make instant adjustments
- Block, allow, shape and prioritize web applications like file sharing, IM clients, streaming media and games
- Deep Layer-7 inspection identifies over 900 applications, and it gives feedback on unclassified applications too